Brief

Резюме
- DORA will soon arrive in Europe, to harmonize and raise the standard of digital resilience frameworks, and it could possibly serve as a blueprint for other countries.
- Given that financial institutions outsource many key services, DORA’s sharper focus on third-party risk management underlines the need to take a more holistic approach beyond internal systems.
- Some banks might view the new regulations as a hindrance to innovation and be tempted to do as little as possible in response. That would be a mistake.
- Instead, DORA offers an opportunity to address deeper underlying issues that raise risk and costs today, by overhauling risk and compliance programs to include intelligent automation and cut back on redundancies and red tape.
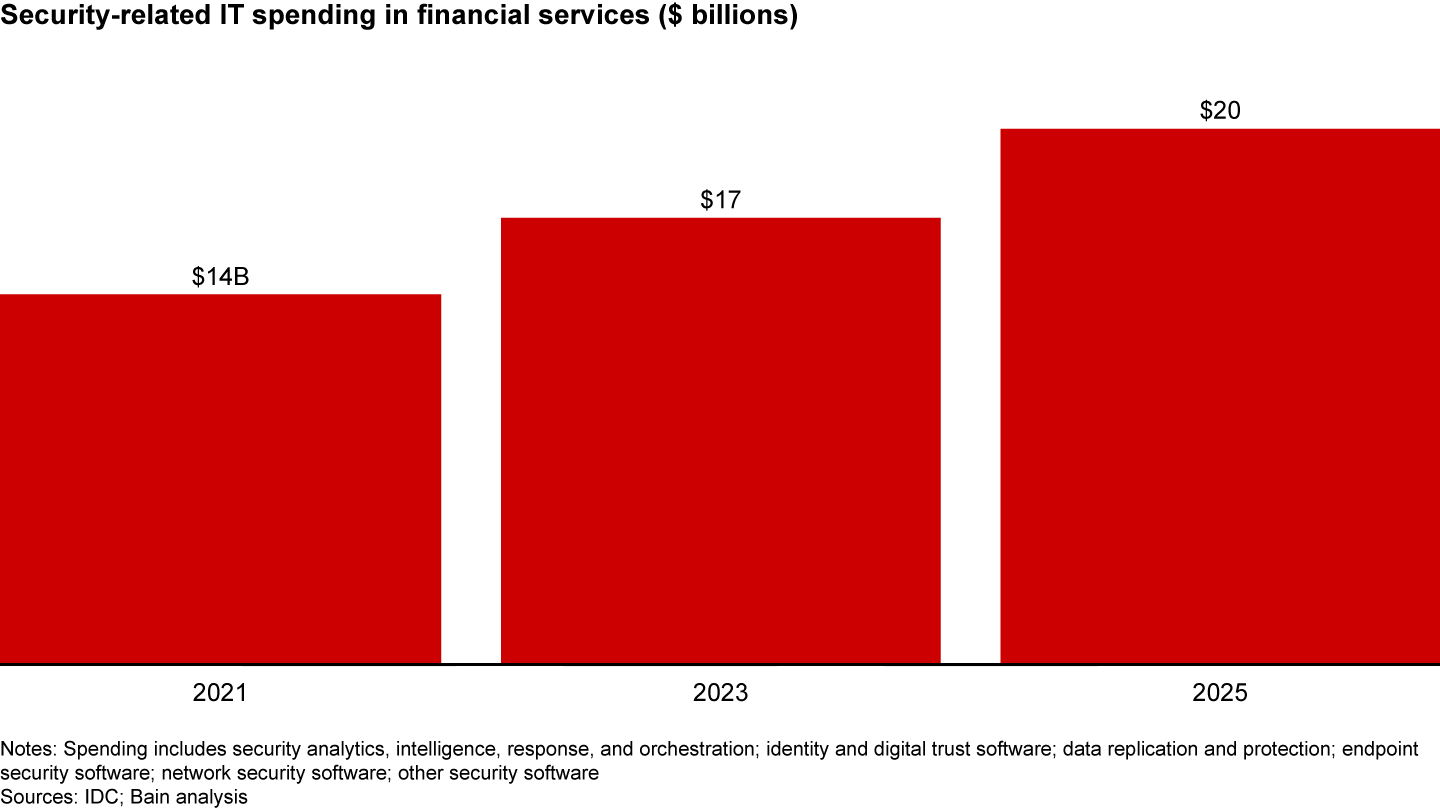
Operational resilience is not an option for banks—and it shows in their spending. Some large banks are each spending hundreds of millions of dollars each year on cybersecurity alone, with that sum having more than doubled since 2015 in some cases. This trajectory will likely continue in the near future at annual growth rates of about 10% (see Figure 1). A considerable portion will go to cloud security, reflecting the shift to cloud-based business models.
The rationale for higher spending is to combat data breaches, which are hugely expensive and undermine trust in banking relationships. The rise of online services spurred by Covid-19 has accelerated this trend, with global cybersecurity venture funding approaching $10 billion. Trust continues to be a key factor in banking, and trust needs to be earned. More broadly, resilience entails a comprehensive perspective on operational risk management, rooted in a sound understanding of a bank’s strategic priorities and technology agenda.

Enter DORA
Compared to most other industries, financial institutions already spend considerably more on cybersecurity. But how effectively? Increasing the cost efficiency of cybersecurity spending by even just 5% each year would represent a huge opportunity to boost the bottom line and valuation of any bank. And since potential damages can reach billions of dollars, resilience makes sense defensively as well.
For financial institutions in Europe, the imminent arrival of the Digital Operational Resilience Act (DORA) could bring this challenge to a head.
Some European banks will recoil inwardly, viewing the new regulations as a hindrance to innovation and pointing to the major sums they already spend on meeting regulatory requirements. They may be tempted to do as little as possible.
But treating DORA as yet another exercise in regulatory compliance would be a mistake. Instead, it could foster a strategic effort to effectively improve resilience. By driving out waste and inefficiency from risk and compliance programs, banks could better withstand a range of shocks, from cyberbreaches to pandemics to supply chain breakdowns.
With DORA, the EU continues to forge an oversight framework for banks’ information and communications technologies (ICT) risks, including for critical third-party service providers. While the rapid pace of digital innovation has benefited customers in financial services, it has also introduced new operational and systemic risks related to a highly connected vendor landscape. As Joachim Wuermeling, executive board member of the Deutsche Bundesbank, phrased it, DORA’s primary objective is to “bring consistent rules and oversight to the seemingly boundless sky beyond the clouds.” And DORA may serve as a regulatory template for other countries to rein in risks associated with increasingly digital operations.
Other countries should take note. Europe has been at the forefront of regulation concerning emerging risk categories such as data protection and privacy, data quality, as well as climate-related and environmental risk. As digital operational resilience is now receiving more scrutiny, DORA could serve as a blueprint for regulation in other parts of the world.
What DORA covers
DORA overlaps with and unifies key elements of existing digital resilience frameworks and standards within the EU, as well as adding new requirements. It aims to harmonize and raise the standards in order to provide a consistent framework.
For example, DORA significantly broadens the definitions of risk covered by the European Banking Authority, explicitly emphasizing networks and any technology-dependent tool or process, in addition to information systems. Moreover, DORA mandates that financial entities considered “significant” by authorities put in place threat-led penetration testing (TLPT), beyond basic testing procedures. TLPT will require preparation such as agreeing on scenarios with regulators and making sure critical third parties are involved.
While we focus here on banks, DORA will apply to the entire financial services industry—not only lending and credit institutions, but also payment and e-money institutions, investment firms, insurance and reinsurance firms, as well as third-party service providers.
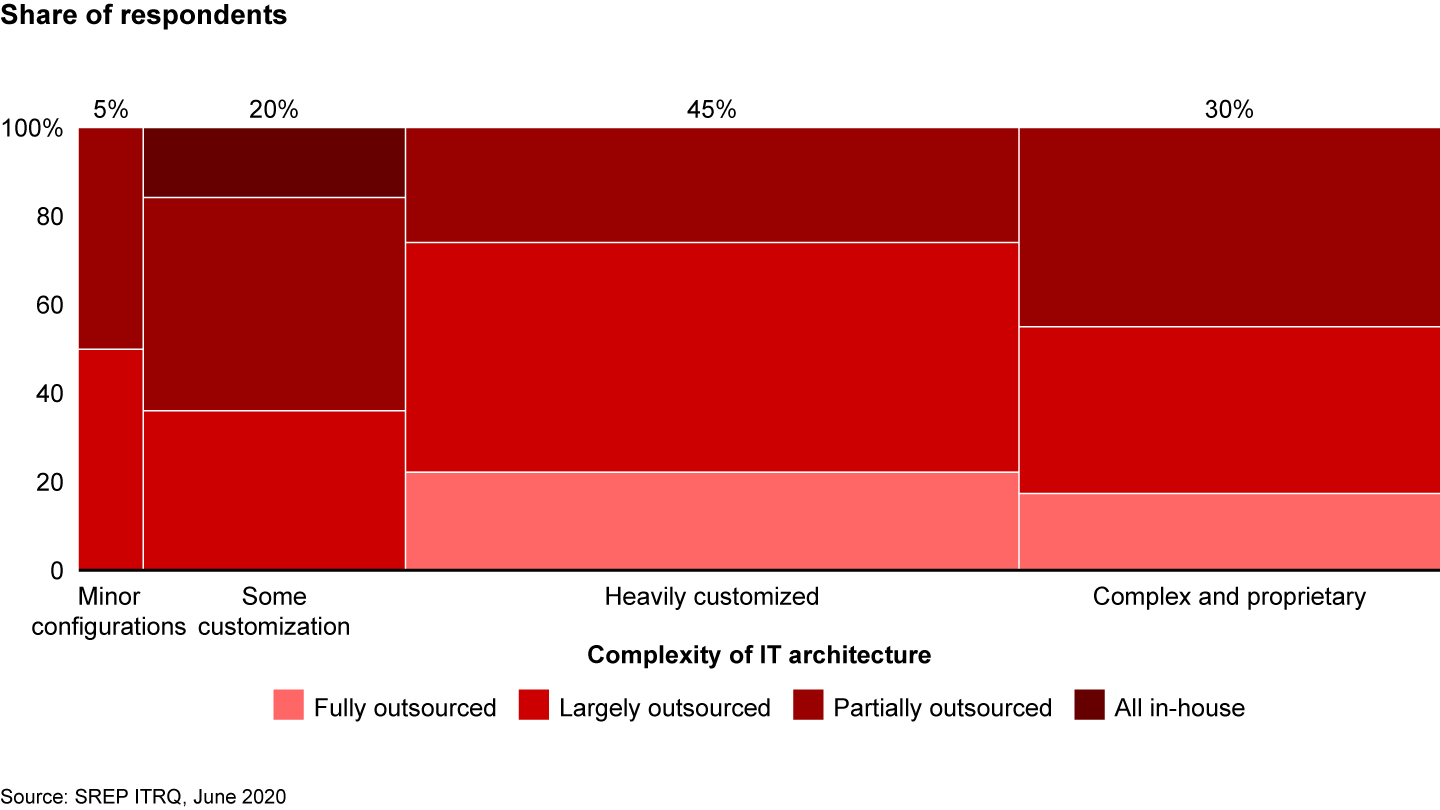
Financial institutions tend to outsource much of their IT and deal with complex architectures. For example, the majority of significant European Central Bank–supervised institutions with heavily customized IT reported that they outsource a large portion of key services to third-party providers (see Figure 2). DORA’s sharper focus on third-party risk management underlines the need to take a more holistic approach beyond internal processes and systems.

Currently, DORA is a draft for consultation, with formal adoption expected later in 2022 and final implementation by 2024. It consists of requirements in five main areas:
- ICT risk management. Operational risk broadly encompasses risk factors related to a bank’s people, processes, and technology. To comply with DORA, financial institutions must maintain digital operational resilience, with an expanded and more granular risk definition that includes malfunction, capacity overrun, failure, disruption, impairment, misuse, and loss.
- ICT incident reporting. Financial institutions already must collect data on and report major ICT incidents to authorities and act on supervisory feedback. Under DORA, they must extend this to incidents within critical third parties. We expect this change to significantly increase the volume of issues to report on.
- Digital operational resilience testing. Financial institutions will complete such testing, with broader threat-led penetration testing including third-party service providers, to help assess whether their cybersecurity is fit for purpose. This will require ongoing review, in light of the rapidly changing nature of threats.
- ICT third-party risk management. Critical third-party providers must be held accountable for providing services consistent with DORA, which might even require financial institutions to renegotiate contracts or change suppliers. It’s likely that some providers will raise their prices to recoup the cost implications of DORA.
- Information intelligence and sharing. DORA encourages financial institutions to voluntarily share cyber threat intelligence across the industry.
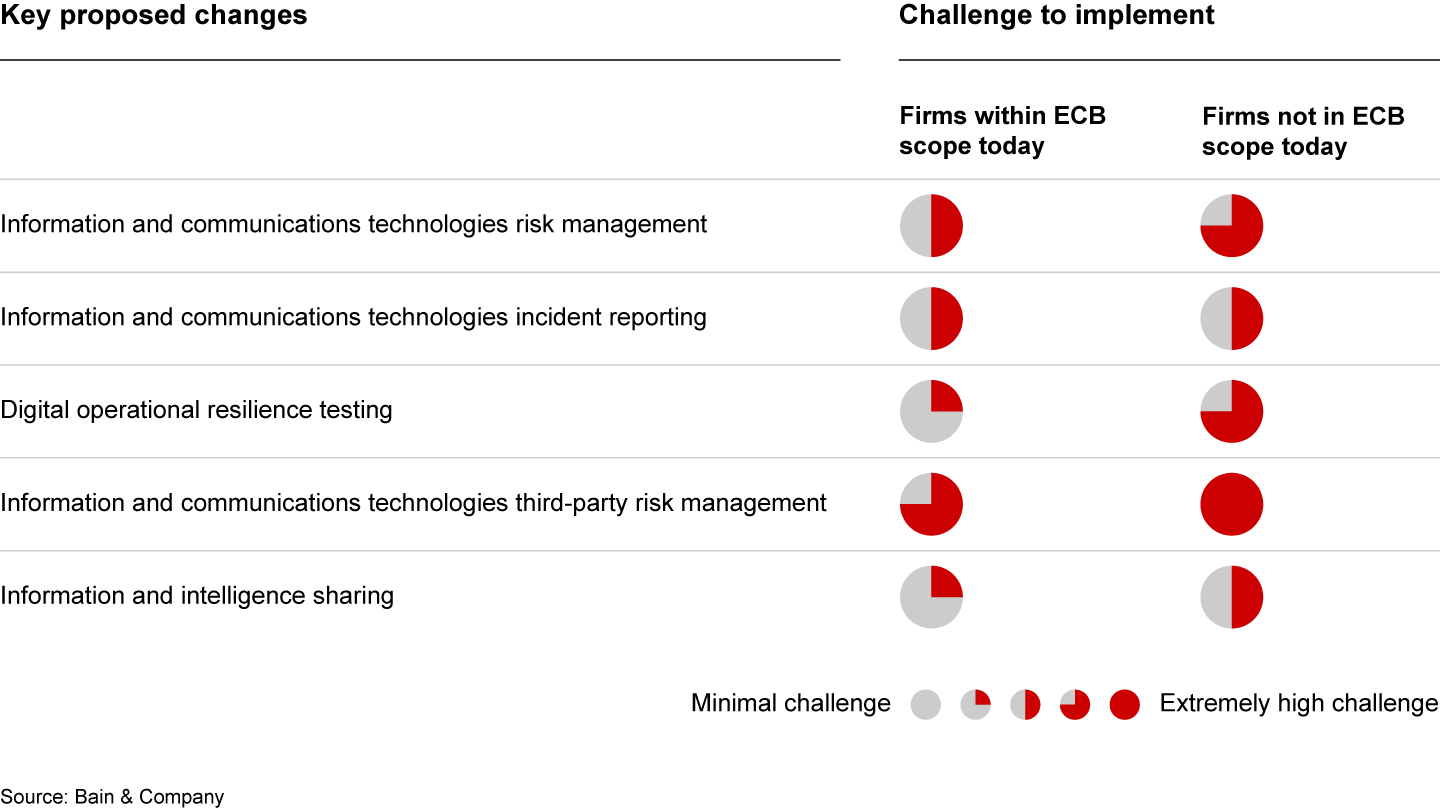
DORA has received many proposed amendments from EU members, generally strengthening and accelerating the requirements for larger financial institutions. In general, firms already within the European Central Bank’s scope may have an advantage relative to others (see Figure 3).
DORA is undoubtedly a challenge, but the real consideration for financial institutions is how they approach it—as a compliance exercise or a strategic opportunity.

Three strategic postures
Banks have three basic options on DORA compliance (see Figure 4). Some might choose to sit tight until DORA takes effect, and then manage any changes through business-as-usual processes. The common rationale here is minimizing current spending and limiting distractions. But the trade-offs include possibly higher operational risk, greater exposure to regulatory action, and a higher potential for complex issues needing to be solved under the close supervision of regulators, perhaps on an imposed tight timeline—all of which add up to a major missed opportunity.
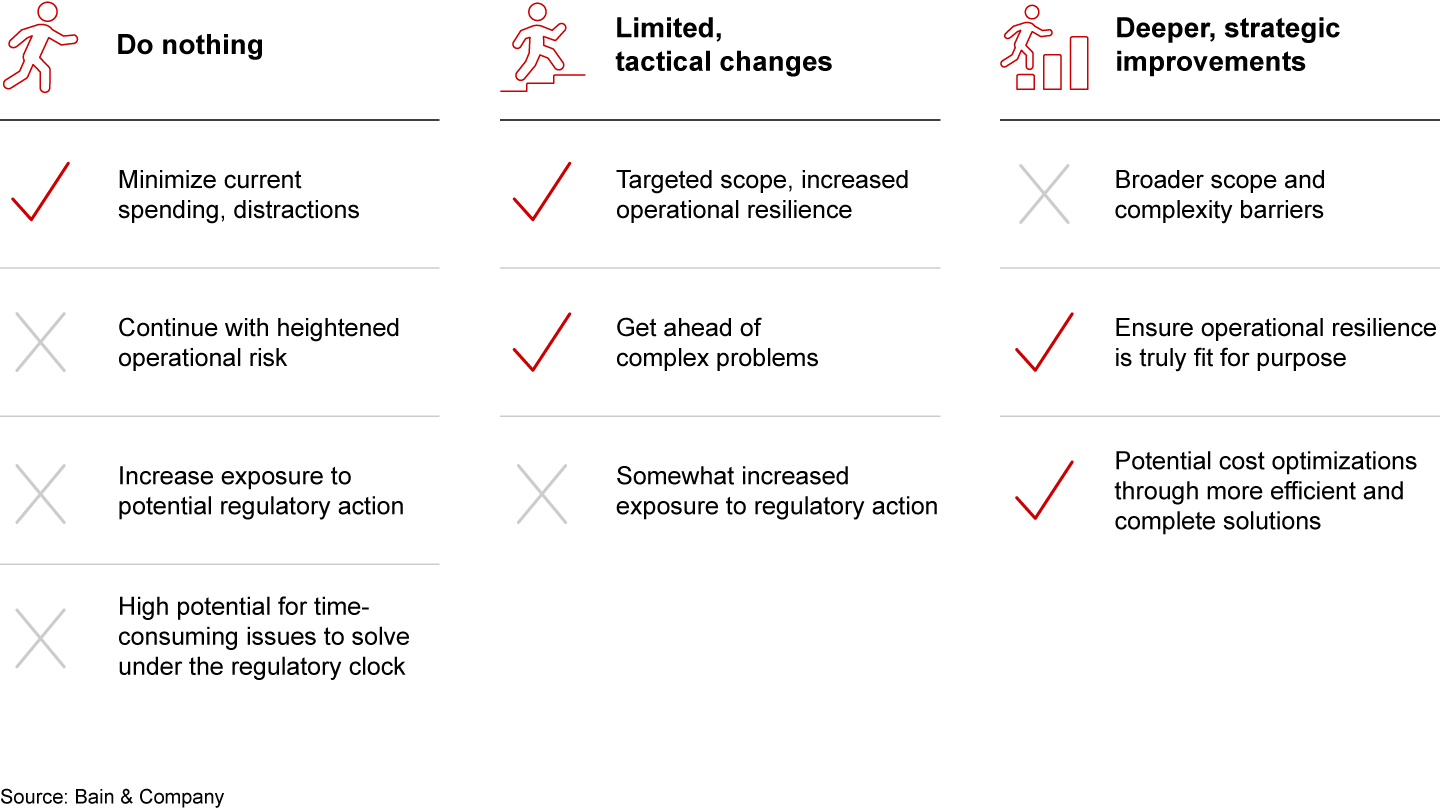

Other banks will implement tactical changes in areas with known gaps, such as third-party risk management. This approach could yield tangible improvements in areas of operational resilience and, if they start now, will provide the time to address such complex areas properly. However, it would not comprehensively address DORA, leaving some requirements to be addressed in short time frames with less than ideal solutions.
Bolder institutions will choose to take the opportunity to address deeper underlying issues that raise risk and costs today and seek to overhaul parts or all of their risk and compliance programs to build a stronger, more efficient organization. True, a broader scope will increase complexity in the near term and expose internal barriers to change. Yet this approach not only ensures operational resilience will be truly fit for purpose, but it also offers cost benefits through more efficient and comprehensive solutions.
Banks have been in similar situations before with regulatory initiatives such as the General Data Protection Regulation and the Payment Services Directive 2. While some financial institutions treated those changes as an exercise in technical compliance, innovative leaders took a more strategic view, enabling them to develop differentiated capabilities in data analytics and platform-based business models. With DORA, laggards of the past might fall into the same trap. The longer-term strategic benefits of digital transformation outweigh the risks by far—provided that banks use digital technology to manage risk and improve overall resilience while cutting back on redundancies and red tape.
Don’t rush to judgment
Many organizations will find that their risk and compliance operating models are far from full compliance with DORA. To stay on top of the situation, financial institutions will have to consider exactly how to foster digital operational resilience. One ingredient will be to establish lean, Agile processes that use automation. Another involves collaboration among the internal functions as well as external partners and technology vendors.
Typically, banks have built their capabilities over time, layering requirement on requirement, so that the resulting compliance engine has many overlapping, complex, and costly components. Not only is this inefficient, but the resulting Frankenstein’s monster of stitched-together mechanisms make real resilience hard to achieve, and the gaps can be difficult to spot and even harder to address.
One large bank, for instance, found that it could save more than 20% on product-related ICT budgets by consolidating disparate efforts aimed at ensuring compliance with various regulations, streamlining underlying platforms, and fully leveraging automation. Realizing these savings, though, entailed more than just identifying redundancies; it also had to break up organizational silos by introducing Agile teams to jointly tackle planning and execution of its digital transformation.
Banks’ digital technology managers, heads of risk management and compliance, and forward-looking strategists thus have some major decisions to make about DORA, and soon. Those who lean toward doing as little as practical will want to be certain, at least, that their third-party providers fully comply with the imminent regulations. They should also ask whether their massive spending on cybersecurity and other operational resilience measures is efficient, with no waste due to excessive complexity.
For those prone to taking more action, but with a narrow focus, the challenge is to ensure they’re focused on the right things and have not missed any major hidden risks or opportunities—both within their organization and among their providers.
The third group will commit to reducing complexity and gaps by adopting a more comprehensive approach, reducing redundancies, stepping up automation, and building a fit-for-purpose operational resilience and compliance engine. That tack will not only help them meet DORA requirements, but also stands to make the organization more resilient and efficient, significantly enhancing its operational risk management capabilities.
Before making the final decision, executives should take the time to review the effectiveness of their current risk and compliance programs from the perspective of holistic resilience, rather than just layering on more DORA-specific complexity. They should prioritize initiatives to close critical gaps, focusing on simplification and improving effectiveness. The first wave of such initiatives would include no-regret moves that depend little on further adjustments to DORA and which can therefore be launched immediately.
* * *
A lack of resilience can make incumbent banks and fintech challengers vulnerable to shocks, and thus impede growth. Addressing the underlying resilience challenge now, which DORA seeks to help address, will lay the foundation for future profitable growth. DORA presents not only a challenge, but also sizable opportunity for banks and other financial institutions that recognize the strategic value of truly fit-for-purpose resilience in increasingly dynamic markets.